Testing is a vital element throughout the software development lifecycle, guaranteeing delivery with as few bugs as possible and making the final product more reliable.
However, more traditional teams still choose to build and run tests only at the final stage of development. This approach is ultimately flawed, because it doesn't support quick feedback and it limits our time, hindering the early identification of bugs, making testing an expensive process and increasing the time to market for the final product.
In order to leverage faster test feedback, testing should be carried out early in the software development lifecycle - this testing strategy is known as Shift-Left and can be applied to both functional and non-functional testing. Shift-Left testing allows developers and testers to work closely together to create and execute test cases in the early stages of the development cycle.
What does Shift-Left mean?
Shift-Left is an approach that moves testing to the beginning of the software development lifecycle (thus “shifting left”). If security testing only takes place when the code is ready for production, it can be too late to go back and fix problems quickly. This can lead to delays, security problems and silos between security and the rest of the DevOps teams.
In other words, it's a strategy in software development that aims to improve delivery quality, as well as to prevent and solve problems as early as possible in the development cycle.
Everything becomes clearer when we visualise the image below:
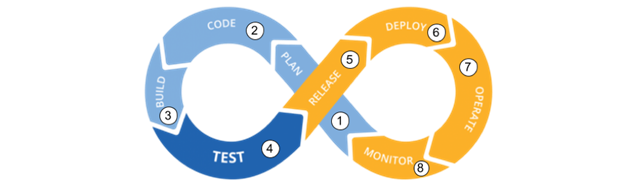
On the left-hand side, Shift-Left is put into practice, where development is made up of the planning, coding, building and testing stages.
This approach was first adopted in concepts such as Test-Driven Development (TDD) and Behaviour-Driven Development (BDD) but is now being applied in different areas. Continuous Integration/Continuous Delivery (CI/CD) platforms allow teams to deploy and use tools to carry out verifications and tests at each stage of the flow.
Related methodologies
The Shift-Left approach is made up of four methodologies that aim to solve problems at different stages during the software development cycle. These are:
-
Incremental: for large, complex systems that integrate with specific hardware. It makes it possible to ensure that each segment is validated before the next one is incremented.
-
Traditional: for lighter validations and less complex systems. Its purpose is to validate stages of unit testing and integration testing.
-
Agile/DevOps: it is based on tests carried out in sprints, and restricted to development and non-operational testing.
-
Model-based: unlike other methodologies in which testing takes place during development, this one validates requirements, architecture and design.
When can Shift-Left be applied?
As organisations try to migrate to a more DevSecOps structure, it is essential to bring security testing earlier into the development lifecycle. The way to do this is by integrating security testing into deployment pipelines, so that code is tested continuously, not just in comparison to other commits in the shared repository, but also in terms of security as a whole.
Continuous Integration (CI) is a process that raises and defends the flag of improving code quality through deployment pipelines. Security can be integrated into these pipelines at the start of the process. Knowing this, we can integrate Shift-Left into continuous integration pipelines such as:
-
Static Application Security Testing (SAST): it’s a way of automating security through continuous integration. SAST analyses the source code and allows developers to solve problems early in the software development lifecycle. In GitLab CI, for example, the deployment pipeline verifies the SAST report and compares vulnerabilities between the source and target branches. These findings appear in the merge request.
-
Dynamic Application Security Testing (DAST): a black box testing methodology used to uncover possible security flaws through automated scanning on a running target (it usually works together with SAST). While SAST analyses source code, DAST analyses runtime errors in running applications. Once an application is deployed, it is exposed to new forms of security risks, such as cross-site scripting or broken authentication flaws.
-
Threat Modeling: it’s the process of thinking about every decision made in a given system and extrapolating how they might affect its security profile, either immediately or in the future. It is a process based on the following objectives: (1) identifying security requirements, (2) identifying security threats and potential vulnerabilities, (3) quantifying the criticality of threats and vulnerabilities in order to prioritise remediation methods. Threat modelling methods create these artefacts:
-
An abstraction of the system.
-
Profiles of potential attackers, including their objectives and methods.
-
A catalogue of threats that may arise.
-
-
Security architecture review: phase responsible for identifying, assessing and mitigating risks to strengthen an organisation's security measures against present and emerging threats and risks.
-
Container image scanning: analysing a container image, layer by layer, to detect possible security threats.
-
Code signing: method of placing a digital signature on a programme, file or software update so that authenticity and integrity can be verified during installation and execution.
There are also other types of security tests such as Interactive Application Security Testing (IAST) and Runtime Application Self-Protection (RASP). IAST operates by placing an agent inside an application and RASP is more of a security tool placed inside an application that can respond to live attacks.
Shift-Left benefits
Practically speaking, the Shift-Left concept aims to find and fix vulnerabilities at an early stage, when code is being written. This not only guarantees better security, but also improves the user experience by delivering software faster, more frequently and with impeccable quality.
Basically, it speeds up development efficiency and can also reduce overheads by detecting and resolving software bugs earlier in the development cycle.
To summarise, these are the main advantages:
- Bugs, defects and performance problems can be identified early in the development lifecycle, making them easier to fix.
- Testing and maintenance costs can be significantly reduced with early detection.
- The final product is of higher quality, with very few bugs and performance problems.
- Time to market is reduced due to testing integrated with development with rapid feedback.
- Improved customer satisfaction with the user experience.
Conclusion
Shift-Left testing supports Agile teams and DevOps practices, while generating better quality products with reduced cost and time. We also need to consider that the concept is popular in the testing community, because it aims to find problems earlier with lower correction costs. Among DevOps, it is also being increasingly adopted.
However, what worries most of them is that it slows down the development flow and makes it bureaucratic to launch a new feature into production. Load testing with the Shift-Left approach is a very sophisticated strategy to ensure that your application is always optimised for best performance.
But tools like this are designed precisely with Agile development in mind, so you have to consider that a few minutes added to your pipeline can bring significant security gains, guaranteeing the quality of what will be delivered to the end user and avoiding problems in your application.
What about the Shift-Right approach? Find out what it is in this article.

